Introduction
Let the business belong to any type of industry; it is a well-known fact that it requires many applications, websites and systems to perform critical business tasks and for a seamless administration. From project management systems, CRMs, Marketing, Bookkeeping, and Internal communication systems to Accounting tools, Analytics apps, and Software development tools, businesses need many applications for a smooth running of their everyday tasks.
Most businesses are taking up cloud-based working styles as it has many extensive advantages like remote working, balanced communication between branches and more . Cloud-based working systems come with both benefits and challenges. One of the main advantages: is that the portability of cloud apps makes it possible for anyone to work from anywhere with a stable internet connection, and the main challenge is data security.
Protecting sensitive business data becomes a top priority, as most business tasks and communication depend on the internet. But adding up additional security controls and multi-factor authentication will make the access point of the applications more complex.
It might require your employers and managers to sign in to multiple systems every day, which can probably push them into frustration and might affect their productivity. And another challenge is that it is hard to remember multiple credentials, and employers can lose track of them, resulting in IT administrators getting piled up with password resets requests.
Data security is a vital concern, and adequate security measures should be enabled, but it can’t done at the cost of your team’s increased frustration and productivity. The challenges with multiple sign-ins and credentials can be solved with Single Sign-On solutions (SSO). SSO is the appropriate solution to bolster security while maintaining end-user productivity.
With an SSO, your employees need not worry about losing track of multiple credentials of various applications, and your IT team can keenly focus on strategic support tasks.
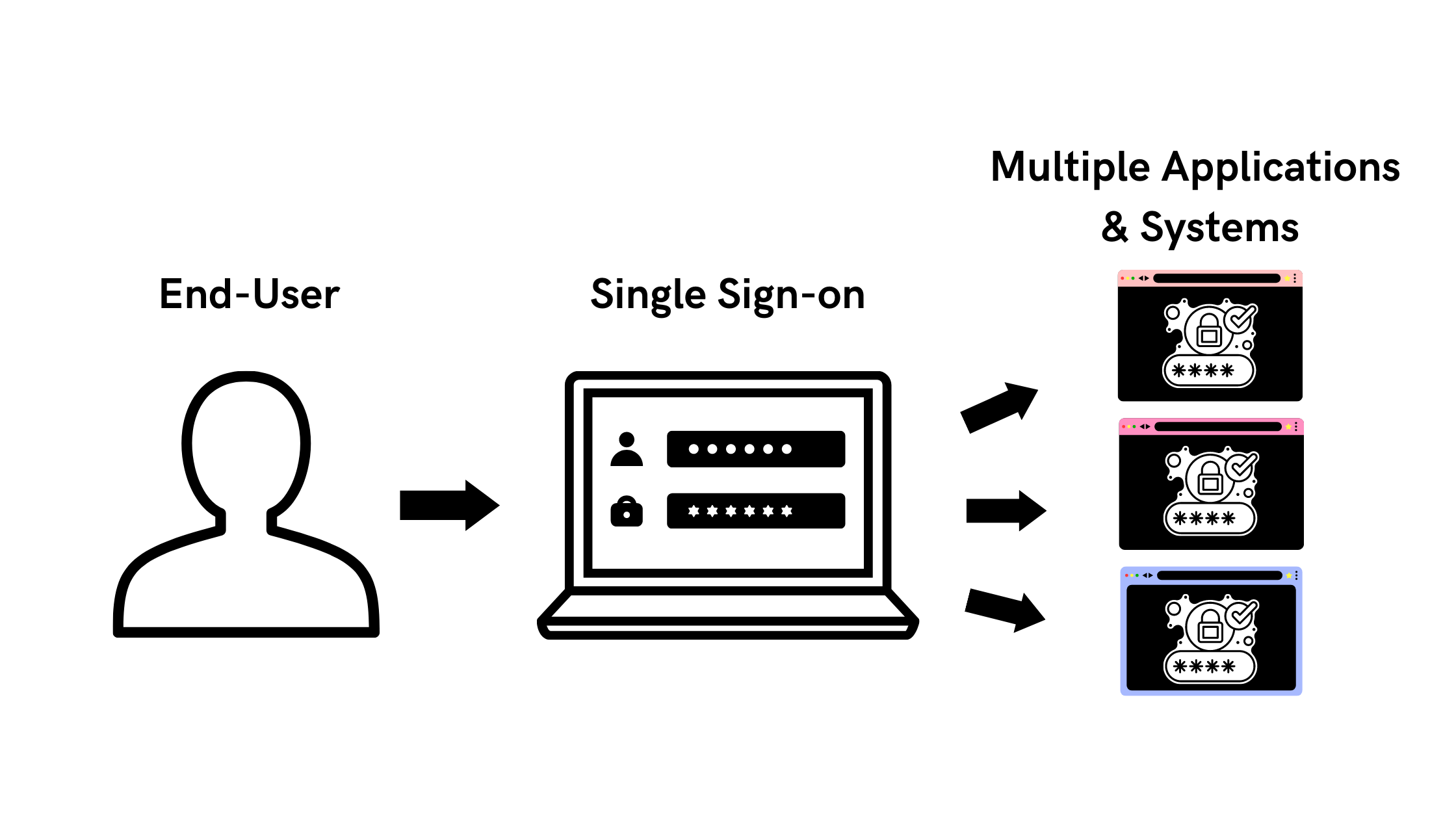
Single Sign-On (SSO) is an authentication technology that allows users to promptly access multiple applications using a single set of credentials (Id and Password). Briefly stated, once the SSO has been set up, users can sign-on through the SSO gateway, which gives instant access to other configured apps, websites and systems that the organization is connected with.
DMG has been providing effective SSO solutions to businesses across industries, resulting in improved security and protection of organisational data. It has also essentially helped businesses let their employers have a solid painless experience accessing enterprise-related systems.
How does Single Sign-On Work?
SSO systems work based on a security relationship that is established between the authority that carries the identity information and can authenticate the user (identity provider IdP) and the application the user wants to access (service provider SP). Instead of communicating the sensitive passwords back and forth across the internet, the user authenticates with the IdP, which creates a centralized session for the user. This session can be re-used by all other connected service providers and can be cryptographically validated.
So when an SSO-verified user tries to access another application, the SSO system provides the already existing session instead of requesting another login. This process provides the users with a seamless experience, allowing them to concentrate on their productivity rather remembering and entering the credentials.
Purpose of SSO
The primary purpose of an SSO is to give the users the authentication to access various apps and resources within an organization’s systems using a pair of credentials. Along with this purpose, SSO solutions come with lot more advantages like
- Authorization to allow or restrict access to certain resources based on user roles
- Centralized user management
- Support for multiple authentication protocols to connect to other identity providers
- Connect legacy systems to integrate with user databases
Benefits of SSO
Time efficiency and improved productivity
Usually, employees use multiple apps, tools or systems throughout their workday, and it requires them to spend a notable time logging in to each of them. It can also be challenging for the employees to remember a number of credentials, and if the credentials are forgotten, it again requires a long time to reset the passwords.
With SSO, end users (employees) need to remember only one set of credentials, and when they get verified with the SSO system, they can avoid the extra time spent logging in to every other app individually. So ultimately, SSO increases employees’ productivity.
Minimize help desk tickets for forgotten passcode
Typically, the IT team regularly changes the internal systems and applications’ passwords. But it becomes more frustrating for them if they often get a request from employees to reset the forgotten passwords. With SSO, this can be reduced desirably as they need to remember a single user id and password.
Decreases IT costs
Garner, in its recent study, revealed that 50% of all help desk calls are with regards to forgotten passwords and resetting them. Another study by Forrester says that a single password reset costs up to 70$. So, with SSO, employees can easily remember the single sign-on password, which will help alleviate considerable IT costs.
Improved security
With SSO, password-related hack is minimized. As SSO eliminates the requirement of multiple passwords and passcode fatigue, users can create a single solid, complex, hard-to-guess passphrase for their SSO accessibility. SSO also allows the IT admins to have central control, with which they can easily view and change the access levels of the users. In case of employees leaving their job or customer contract ends, admins can easily restrict their access to them instantly.
Enhanced Customer Experience
If you have multiple services providing business, you can provide SSO-implemented access to your customers. For example, in a university, students will have multiple access points like classrooms, libraries, labs, a cafeteria, a hostel, etc.; if students need to have a separate id and password to access the systems in these places individually, how frustrating it could be! With SSO, businesses can provide their customers with a seamless experience as they can access every service they offer under a single credential.
Can SSO and MFA work together?
Single Sign-On (SSO) and Multi-Factor Authentication (MFA) can work hand in hand. These two are the most entrusted solution available today to secure data. MFA is an authentication technology that requires the users to provide two or more verification credentials to get access.
Implementing SSO and MFA together can enhance security by limiting the frustration of users and also allows the IT department to monitor the network activity. While MFA maintains tight security and manages the user identity, SSO will increase the password strength and limit password fatigue.
At DMG, we recommend that businesses implement SSO and MFA as part of their cyber security strategy.
Organizational SSO vs Social Logins
Social Logins and SSO are different authentication methods that allow the end-users to access the related systems and applications.
Social Login allows the users to log in to various websites and applications with a single click using their existing accounts from various social providers like Google, Hotmail, Facebook, etc.
Advantages of Social Logins and SSO for Business
|
Social Login
|
SSO
|
|
Supports only limited social Id providers
|
Auto Scalable to 100M users
|
|
Easy-to-manage admin console
|
Peak load of 240000login requests/second
|
|
Native mobile support and responsive apps
|
Web and Mobile SSO
|
|
Maintenance-free social APIs
|
Supports SAML, 0Auth 2.0, JWT, Multipass & more
|
How to choose the SSO Products?
Choosing the right SSO product can be quite tricky. There are multiple SSO products available in the market today. Every product comes with its own pros and cons. You need to understand what the solutions offer with regards to their features and select the one which satisfies your requirement. Here are a few factors that businesses need to consider when selecting an SSO product.
Customizations
To provide the users with a better user experience, the SSO solution should let the business customize and adapt the login screen to the brand’s look and have the possibility to add additional features like MFO.
Endless Integrations
SSO solution should allow every in-house system to be integrated seamlessly. If they don’t have the permissions to integrate any system businesses use, then it becomes hard to achieve the single credential aim.
Multi Device Experience
With employees and customers having the possibility of accessing the systems on various devices such as laptops, mobile or Tablets, SSO solution should be compatible with every device.
Security
SSO should encrypt the user data and support MFA to prohibit any possibility of password hack.
Scale
SSO products should support the businesses when they scale up. So it is unpredictable when the user will scale up, so SSO should be able to accommodate new users without any trouble.
Along with these factors, you need to look for still few mandatory technical features like
- Group-based control
- Authentication via SAML
- Pre-built and custom connections to SAML apps
- Conditional access policies
- Authentication via LDAP
- JIT and SCIM provisioning
Top 5 SSO Products
In no particular order, we have listed the five best SSO products available in the market today
Ping Identity
Ping Identity is an identity and access management platform with multiple products. With Ping Identity, SSO users can access any application or service, be it SaaS, on-prem, mobile apps, software tools or APIs. With their SSO product, businesses can integrate MFA, password-less authentication, and API security. They mostly partner with large global level corporates and provide SSO solutions for in-house requirements or customer-based cloud options.
Auth0
Auth0 is an authentication as a service platform that solves complex and complete large-scale identity and access management and develops SSO solutions for global enterprises. It’s UPS is it’s easy to integrate the platform. In most cases, Auth0 runs in their public cloud, but now, they also run the SSO services in a private cloud.
Keycloak
Keycloak is an open-source identity and access management platform. It is largely based on a community that is backing Keycloak and is constantly being enhanced upon the community. Although Keycloak is now mostly utilised as an on-premises solution, the group is also trying to include cloud-native compatibility soon. Its key features are user federation, strong authentication, user management, fine-grained authorisation and more.
Okta
Okta is a cloud-based authentication solution that can be integrated with business identity systems along with more than 4,000 corporate apps that most businesses use. It provides a scalable framework that enables businesses to establish authentication for massive services. In addition to integrating with AD, LDAP, and HR systems, Okta provides IT staff with a single central interface via which they can observe and control user access. Okta has recently acquired Auth0 and together cover diverse digital identity use cases, provide secure access, and ensure security.
Amazon Cognito
Amazon Cognito is an identity and access management solution available on AWS. Advanced security features like risk-based adaptive authentication and compromised credentials protection are also available with Amazon Cognito. For significant events, such as sign-ups, sign-ins, risk scores, and the outcomes of sign-in attempts and second-factor challenges, Amazon Cognito can additionally store metrics and data in Amazon CloudWatch.
Overview of Comparisons among the SSO products based on features
Compliance is one of the important drivers for deciding the SSO product. Depending on the business nature and customer data that needs to be stored in SSO, it has to be compliant with certain regulations. So, here is a comparison of SSO products based on compliance with regulations when the solution is hosted in an organised environment.
When compared, compliance being one of the major prerequisites of an SSO product, it is important for businesses to choose a product that is compliant with various broad regulations.
Pricing:
- With Ping Identity, businesses need to buy a license per product according to their catalog. The prices per license are not openly available.
- Auth0 comes with a freemium plan followed by two premium plans that come with additional features that are essential for large businesses. Pricing in Auth0 is defined based on the number of users. It also has an enterprise plan that offers a high SLA environment with enterprise-grade support, compliance with various standards and more extensive log retention. With the price of the premium plan available on their official website, businesses need to contact them directly for an enterprise plan.
- As Keycloak is an open-source solution, it is free to use.
- Amazon Cognito charges every month in regards to the active users.
- Okta has a differentiated pricing system between in-house usage and customer-based SSO. Each identity has various price plans, and they can be verified on their official website.
While comparing, all the five products have a different system of pricing, so depending on the other features, businesses need to choose a plan that will be best for them.
Protocol Support: When selecting an SSO product, it is important to check its relationship with various important protocols as they are the basic requirement to connect to other identity providers.
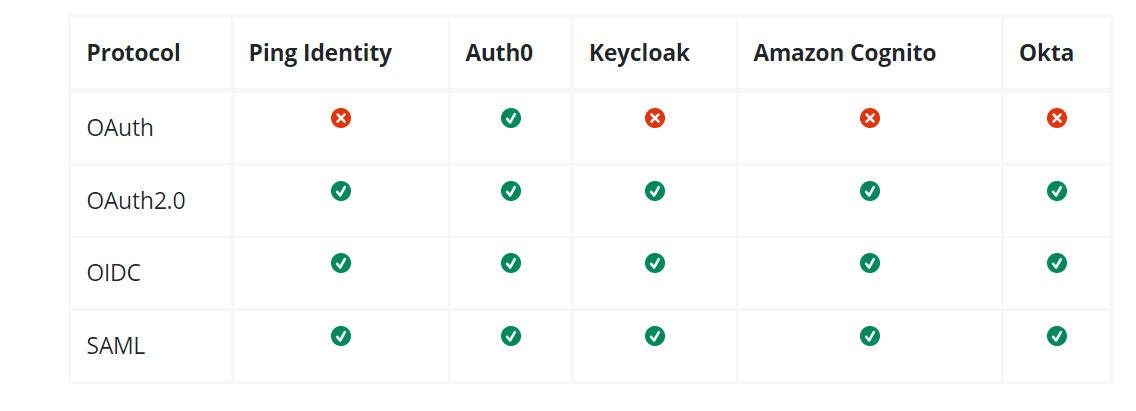
Almost all the SSO products support the most important protocols. Businesses can check on the protocols they require to connect with the identity providers and then select their SSO product.
MFA Support: We have already discussed how a combination of SSO and MFA will provide a multitude of user experiences and security. So it is important to check whether the SSO product is compatible with integrating MFA or not.
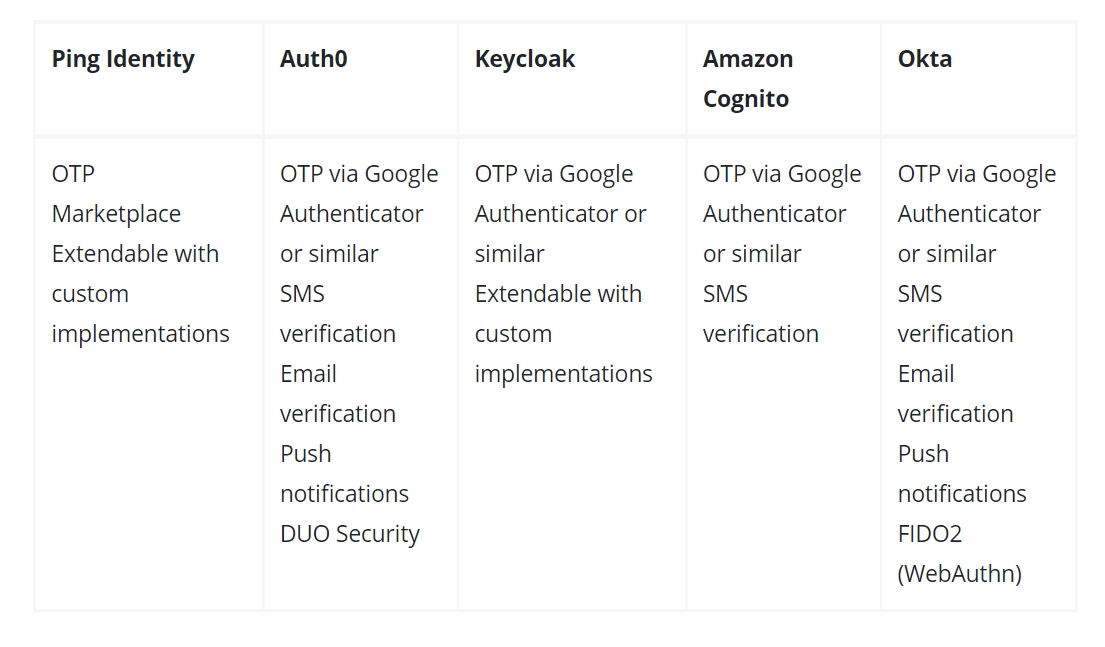
All the five SSO products support MFA through OTP via google authenticator and similar apps. Few products offer additional features like SMS, push notifications and more. Businesses can decide on what type of MFA will make their data more secure and choose an SSO accordingly.
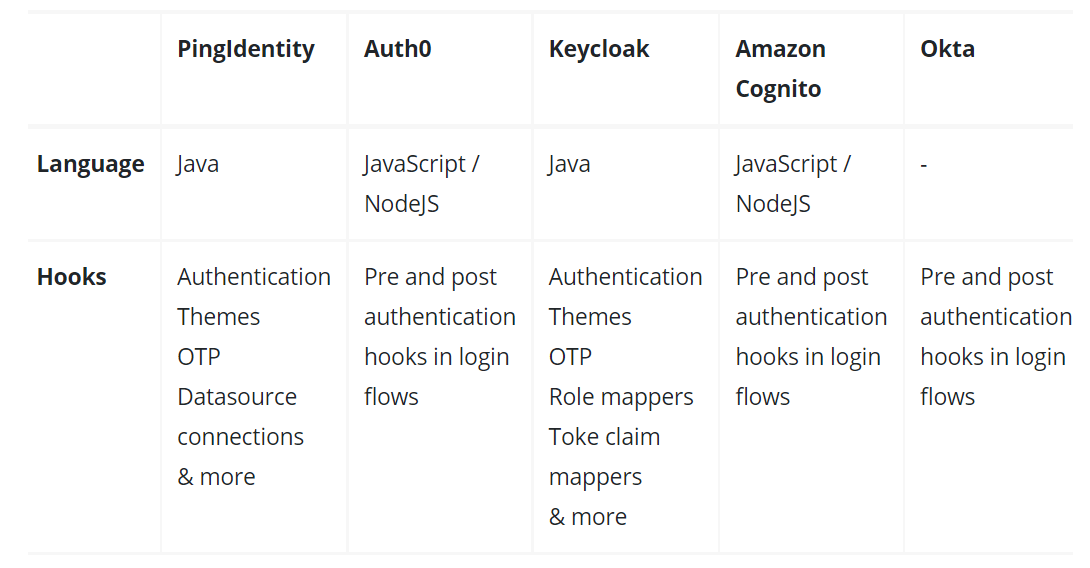
Integrations: Integrations are the core necessity and basic feature required in an SSO product. Integrating all the applications and systems of a business with the SSO is a complicated process. So, SSO products need to provide extensive support that can save a lot of time and developer costs. Here is the overview of SDKs provided by these five products.
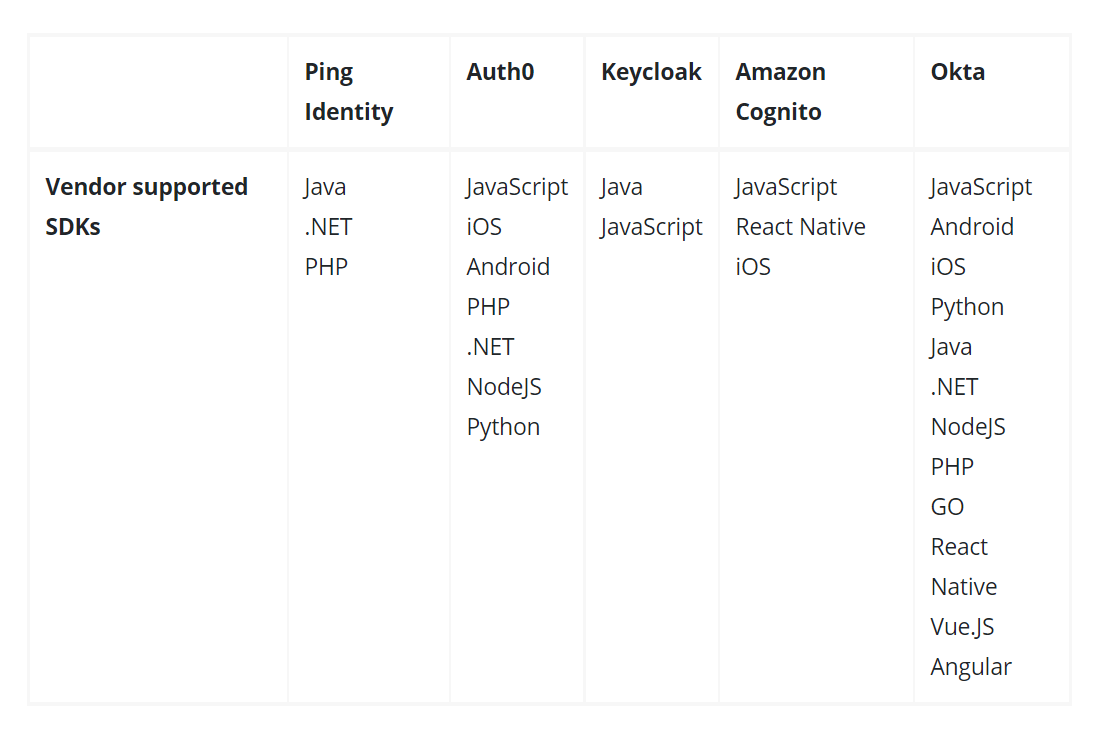
While it may appear that SDKs only support a few languages, it’s crucial to remember that all products implement the aforementioned SSO protocols, and there are a ton of universal libraries for OAuth2.0/OIDC and SAML available for every language.
While this comparison overview is to know the key difference in the features provided by the top 5 SSO products in the market, DMG recommends businesses to take support from an SSO expert in choosing the right SSO product according to their business needs.
How to overcome the challenges?
Overcoming these challenges is relatively easy. With the right partner and guidance, businesses can seamlessly implement SSO solutions without hesitation.
DMG is a trustworthy partner with multi-year experience in SSO consulting and implementation. DMG comes with end-to-end SSO solutions, which include the selection of suitable SSO technology, implementing it, and allowing the users to get familiar with the SSO systems.
DMG aims at a smooth implementation of SSO solutions strictly without disrupting the workflow of the organisations, even during the integration process. After studying businesses’ configured applications, team DMG will come up with the best SSO solutions depending upon the requirements.
With years of experience in consulting and implementing SSO solutions, DMG can be your trusted partner in developing the right SSO solution for your business’s needs. DMG has supported businesses in various industries in implementing SSO solutions for both in-house and customer-based requirements.
